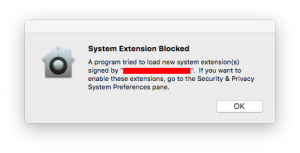
In 2018 Apple introduced secure kernel extensions to their MacOS. Earlier applications could install kernel extensions without the user knowing or specifically being required to “approve” that extension. Think of kernel extensions like drivers and other very deep operating system code that controls significant parts of the operating system. The increased awareness and security of kernel extensions is/was required because malware had begun to exploit these extensions.
Since about MacOS 10.13.4, any kernel extension had to be “approved” by the administrative user of the mac. In general, users had 30 minutes after software install to “Allow” the installed Kernel Extension in the Security tab in System Preferences with a reboot or reload of the extension resetting that “Allow” clock.
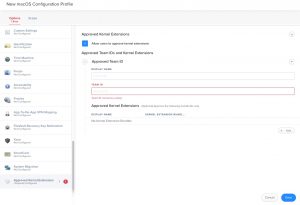
Additionally, Macs that are enrolled in an MDM server can be configured to pre-approve Kernel extensions.
Several things to note:
Kernel Extensions MUST be pre-approved prior to a pushed application install
In order to correctly install software that requires kernel extensions using an MDM server like JAMF, you must first pre-approve the kernel extension before installing the software. There isn’t anyway, either manually or automated, to approve a kernel extension after the fact for software installed with the MDM. Conveniently, newer versions of JAMF provide a very easy way to create a configuration profile to approve the kernel extension just with the associated “Team_ID”.
DEP enrolled Macs happy to comply, User-enrolled macs must be sure to “approve” MDM
For MDM controlled macs, only DEP (Device Enrollment Program) enrolled macs can be reliably configured to avoid asking the user to “approve” the kernel Extension. Macs enrolled in the MDM with any other user-controlled enrollment process (i.e. install package, email invite, etc.) can be in a state where the configured pre-approval of kernel extensions will not work. For example, if the user never approved the MDM profile. Look at the Profiles tab in System Preferences.
Pre-approval isn’t installation
You can pre-approve a kernel extension using an MDM server and that will appear in the “Profiles” tab of System Preferences. However, the kernel extension isn’t actually installed until you install it with the installation process from the vendor. Meaning that it won’t show up in the KextStat or Sqlite commands below until it’s actually installed. (That is probably obvious to most but I spent a good 10 minutes on this before it dawned on me!) Pre-approval of the kernel extension essentially avoids asking the user to approve the kernel extension with the 30 minute timer mentioned above. Essentially, the pre-approval process doesn’t load the kernel extension onto the system it just says that once the kernel extension is loaded/installed no additional approval from the user will be needed.
Uninstalling doesn’t remove from sqlite database
When you uninstall a kernel extension, while the extension may be removed the entry in the kextpolicy database is typically not removed. It can become important to remove these database entries. We have found that kernel extensions, even if unapproved, that remain in the kextpolicy database can interfere with the system when new versions of software requiring kernel extensions are installed. Deleting entries from the kextpolicy database can only be done with SIP (system integrity protection) disabled. See below for the details of deleting these database entries.
Some Commands to know:
Kextstat
Displays all running kernel extensions
kextstat | grep -v1 apple
Displays all non-Apple (3rd party) running kernel extensions
/usr/bin/sqlite3 /var/db/SystemPolicyConfiguration/KextPolicy 'SELECT * FROM kext_policy;'
Displays kernel extensions that are installed by the user manually. The returned format begins:
Team_ID | Bundle_ID | Approved (1=approveded, 0=not approved)
/usr/bin/sqlite3 /var/db/SystemPolicyConfiguration/KextPolicy 'SELECT * FROM kext_policy_mdm;'
Displays kernel extensions that are installed by the MDM server as part of a pre-approval process. The returned format begins:
Team_ID | Bundle_ID | Approved (1=approveded, 0=not approved)
To delete a kernel extension from the kextpolicy database: First disable SIP.
Once booted back into the running MacOS:
> sudo -s
# /usr/bin/sqlite3 /var/db/SystemPolicyConfiguration/KextPolicy
sqlite> SELECT * FROM kext_policy;
OR
sqlite> SELECT * FROM kext_policy_mdm;
THEN
sqlite> DELETE FROM kext_policy WHERE team_id = displayed_team_id_from_above;
OR
sqlite> DELETE FROM kext_policy_mdm WHERE team_id = displayed_team_id_from_above;
sqlite> .quit
#
Remember to re-enable SIP!